Delivered through malicious spam campaigns, Loki focuses on stealing credentials off the victim computer and runs a keylogger. Loki also communicates back to a Command and Control server (C&C) to report what it finds and to receive commands if needed.
How it works
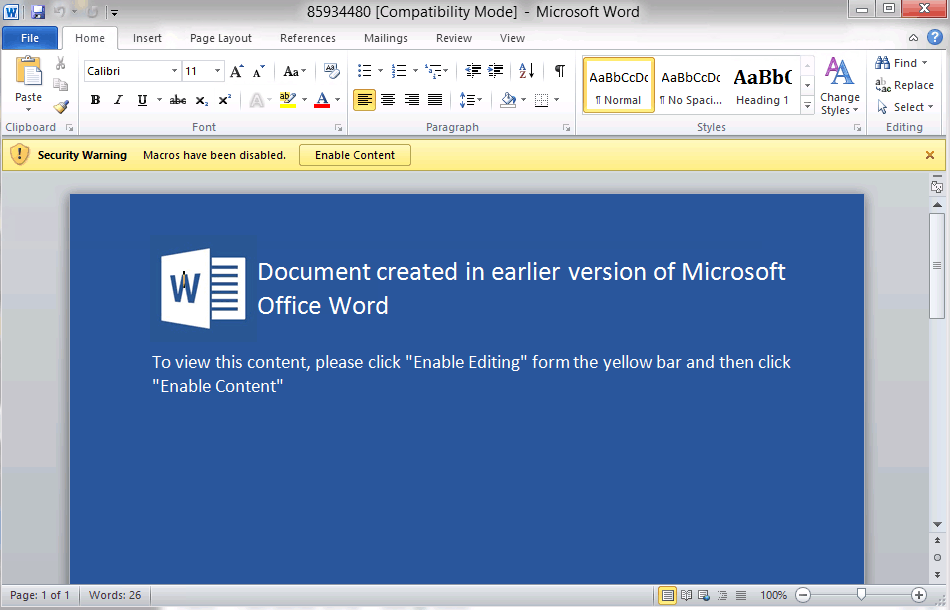
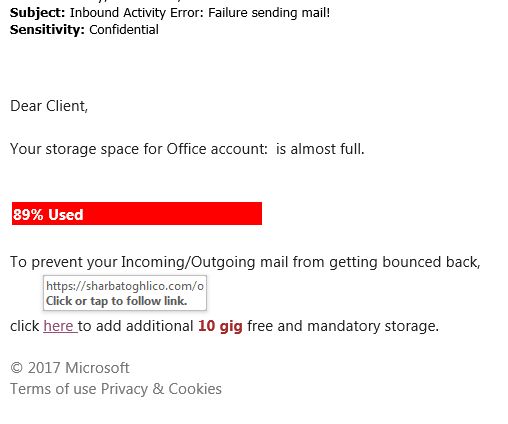
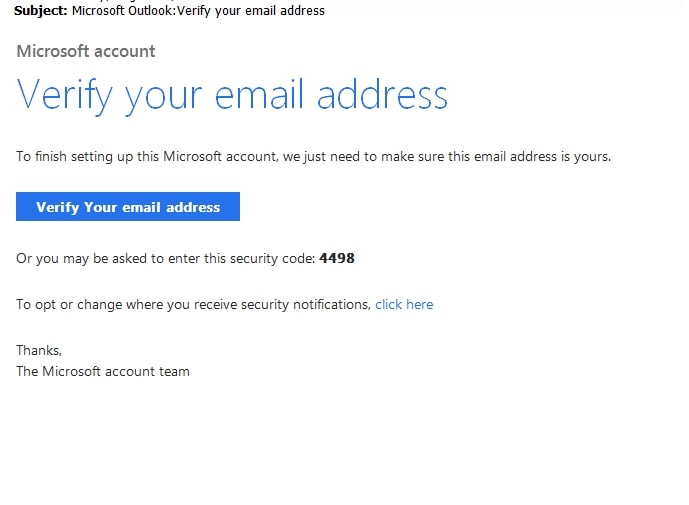
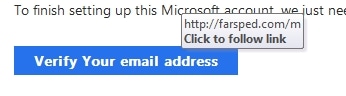
Loki, named after the creator’s username Lokistov, is delivered to users through a variety of channels, but the most common is malicious emails that can come in a variety of types. The most common strategy is the familiar “invoice” style email that attempts to get the potential victim to open the attachment. Once opened, the “invoice” will try to run embedded macros or get the user to follow a link to a downloader. One example of such a “invoice” can be found below.
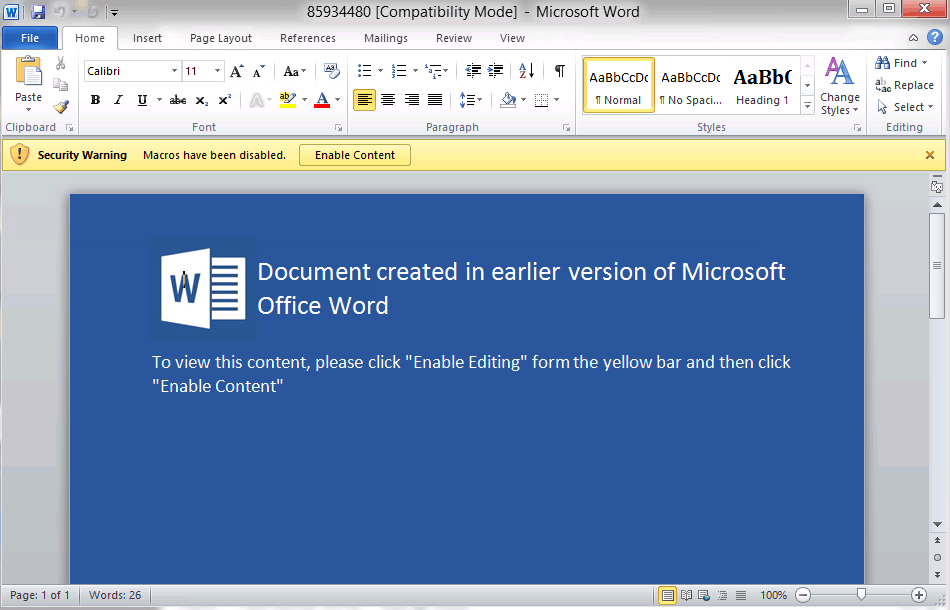
If the potential victim were to click “Enable Content,” Loki would be installed and start gathering data. This is a common attack vector[ and was used by, albeit in a more complex way, Emotet.
This is not the only way Loki can be delivered, however, as it can be purchased by a malicious user, Loki will be delivered in the most cost effective way.
Loki focuses primarily on credential-stealing and boasts an impressive 80 programs it has the ability to steal from. The most notable being all major browsers, including:
- Google Chrome
- Mozilla Firefox
- Microsoft Edge
- Microsoft Internet Explorer
- Opera Software’s Opera browser
In addition to this already worrying list, Loki is able to go after many alternative versions of these browsers such as:
- 8pecxstudio’s variant of Firefox, Cyberfox
- Google’s open-source browser Chromium
- Independently developed Firefox fork, WaterFox
- Nichrome
In addition to browsers, Loki can go after FTP clients, Microsoft Outlook, and independently developed SuperPuTTY. This list will likely be expanded in future campaigns to include more commonly used programs if vulnerabilities are found.
After connecting and confirming the presence of its C&C server, Loki launches a keylogger in a separate thread. This keylogger records every button press of the keyboard during its operation and can be used to reveal other passwords and usernames that may not have been stored in a program it can access. This is then bundled with any other data it retrieved.
Once the data is gathered, it is compressed and sent to the C&C server hosted by the malicious actor. These normally are shut down quickly after a new campaign has been identified but can remain active for days or weeks at a time giving them plenty of time to store the gathered data somewhere else and sell it.
Who is affected?
Loki can be bought in the dark web for fairly cheap. Last know price at the time of this writing was $70. The consequence of this is that Loki can be used to target anyone. The benefit of the availability is it makes it much easier for Anti-Malware companies to stop it.
Indicators of Compromise
- C:\Users\admin\AppData\Local\Temp\saver.scr
- a.doko.moe
- MD5: 500F84B83BE685009C136A67690CA0C3
What you can do
If you or someone you know is infected with the Loki malware download SUPERAntiSpyware Professional right now and get a 14 day free trial, no credit card required. SUPERAntiSpyware is easy to install and will detect and remove Loki from any Windows computer.
If you are a Computer Technician, you may like to try our SUPERAntiSpyware Tech Edition solution, now free for the next 30 days. Use Tech03 as the Tech ID. Click here: https://www.superantispyware.com/technician-download.html
How To Remove Loki
- Restart the infected computer in safe mode without networking.
- Search through the items in the Indicators of Infection section above and investigate any files/folders you do not recognize. You can run the file through SUPERAntiSpyware or online through VirusTotal.com to confirm that it is malware.
- Delete files and folders that have been confirmed as malware.
- Repeat steps 1-3 on all other machines in the network.
- Restore all infected computers to normal mode only after confirming the infection is removed.