
Back in January of this year, the United States Department of Homeland Security advised PC users to disable Java from their web browsers following the serious zero-day vulnerabilities discovered in Java. In response, Oracle released an emergency Java patch, but the fix was not meant to patch all the critical vulnerabilities.
Staying protected against Java exploits is a rising concern among millions of Windows®, Mac OS®, and Linux® users. What makes this exploit such a big deal is the fact that Java runs on more than 850 million personal computers and on billions of devices worldwide, including mobile devices and TVs1.
What is Java and why do I need it?
Java is an object oriented programming language and a cross-platform technology that was designed to have few implementation dependencies. Sun Microsystems released the first public implementation as Java 1.0 in 1995. Since its inception, Java has expanded and has gained immense popularity among more than 9 million2 developers around the globe. The following statistics3 from Oracle can give you a good grasp of where Java currently stands:
- 1.1 billion desktops run Java
- 930 million Java Runtime Environment downloads each year
- 3 billion mobile phones run Java
- 31 times more Java phones ship every year than Apple and Android combined
- 100% of all Blu-ray players run Java
- 1.4 billion Java Cards are manufactured each year
- Java powers set-top boxes, printers, games, car navigation systems, ATMs, lottery terminals, medical devices, parking payment stations, and more.
“From laptops to datacenters, game consoles to scientific supercomputers, cell phones to the Internet, Java is everywhere!” – Oracle.4
Java powers numerous programs ranging from web-based applications, mobile applications, utilities, games, interactive content for websites, to large-scale enterprise applications. The moment you need to use an application or run/access any Java-based content, you need to have Java installed on your device.
So, what went wrong?
At the beginning of this year, researchers discovered a new Trojan called Mal/JavaJar-B that exploits a flaw found in Java, leaving computers running on Windows, Mac OS, and Linux vulnerable to serious attacks. The flaw allows attackers to remotely trigger malicious code which can then infect your machine with malware or even at times ransomware.
Let’s give you a little background on how these types of attacks actually work. Cybercriminals need a way to get their malicious programs into your computer. To achieve their goal, they often exploit security holes in legitimate programs or websites. For instance, cybercriminals can create a malicious web page, or even hack a legitimate website and inject malicious code to exploit a weakness in your browser. When you visit these web pages or websites, the malicious program enters your computer and infects it. In the same way, when cybercriminals discovered the security flaw in Java plug-ins, they started exploiting it to infect computers and fulfill their malicious intents.
Cyber intruders have been exploiting vulnerabilities in Java to execute a series of attacks not just against home-users, but also against companies such as Microsoft, Apple, and Twitter. In February, another zero-day vulnerability was discovered by the security firm FireEye that was used to attack multiple customers. Researchers at the security firm observed a series of exploitations against web browsers having Java v1.6 Update 41 and Java v1.7 Update 15 installed. Unlike other popular Java vulnerabilities, FireEye found that the new vulnerability leads to arbitrary memory read and write in JVM process.
A zero-day attack or vulnerability refers to an attack that exploits a previously unknown vulnerability in a computer program. The attack occurs on “day zero” of awareness of the vulnerability and developers had zero days to address and fix the vulnerability.
It isn’t the first time that hackers have targeted Java. It seems that cyber criminals are firmly establishing the trend of attacking Java to exploit its security flaws. According to security software maker Kaspersky Lab, Java became the most frequently attacked piece of software last year and it was responsible for 50% of all cyber-attacks in 2012.
However, to avoid any confusion, it is important to mention that these vulnerabilities are related to security issues with Java in web browsers (Java plug-ins) and are not applicable to Java running on servers, standalone Java desktop applications or embedded Java applications5.
Should I disable Java plug-ins?
As mentioned earlier, U.S. Department of Homeland Security is actively advising users to disable Java in their web browsers in order to stay protected against such vulnerabilities. In addition, researchers warned that it could take two years for Oracle to fix all the security flaws in Java, excluding any additional Java exploits likely to be discovered in the future.
While Oracle is working on patches to fix known security holes, there are currently no practical solutions to the vulnerability in the software; the only solution that seems available at this time is to unplug Java from web browsers.
However, before you unplug the Java plug-in, there are consequences you should be aware of. If you don’t have Java installed on your system and you try to run or access Java-based content, such as online games, web based instant messaging clients, mobile applications, etc., you will encounter the following warning/error message:
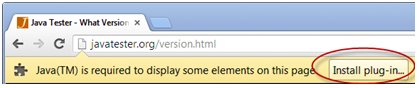

The absence of Java on your machine will completely prevent you from accessing Java-based content. This can be a huge inconvenience, but if you are concerned about security and want to be completely safe from these kinds of attacks, you’ll have to live with this inconvenience until the makers of Java come up with a concrete patch to fix these vulnerabilities.
However, the good news is that you don’t need Java all the time! You need it only when you are interacting with websites containing Java content. If you have multiple web browsers installed on your computer, you can choose to have the plug-in installed in one web browser (the one you rarely use) and only use it to access websites that require a Java plug-in.
Before you get ready to disable Java, you should check to see if you have Java installed on your machine. Visit this URL and click the ‘Do I have Java?’ link to see if you have Java installed.
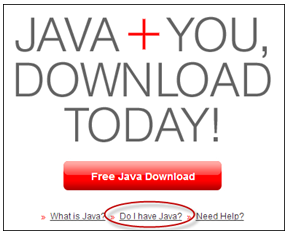
If you have Java installed on your computer, you’ll be shown which version of Java is installed, and you’ll also be notified if a new version of Java is available for download.
How do I disable Java in my web browser?
Fortunately, unplugging the Java plug-in from the web browser is very straightforward. If you have Java v7 Update 10 or later installed on your computer, you can disable Java in all web browsers using the Java Control Panel. To access the Java Control Panel, follow these steps:
- Click “Start” then click “Control Panel”.
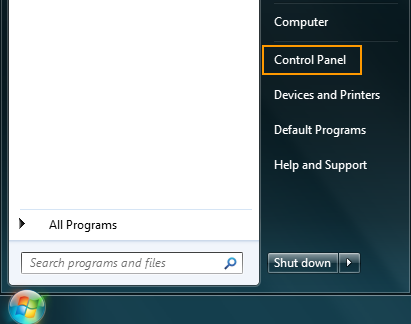
- Locate and launch “Java”.
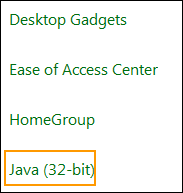
- Click the “Security” tab.
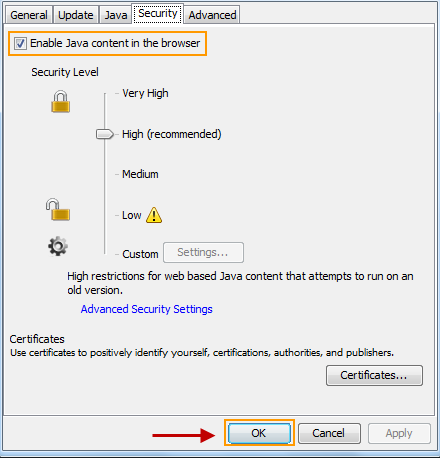
- Un-check the “Enable Java content in the browser” checkbox. Click “OK” and you are done!
To completely uninstall Java from your computer or to disable Java plug-in on an individual browser, please use the links given in the next page for for step-by-step instructions:

Is Java the reason my video playback is very choppy?
@aac9929fa29b0ee1bdb21956447d40fb:disqus There could be many reasons for choppy video playback! Try the following:
1. Try disabling unnecessary plug-ins/add-ons.
2. Update the Java plug-in and Adobe flash player to latest version
2. Switch to a different web browser( may be Google Chrome?) and check if the issue persists.
Verry, very, very, very, very, VERY little chance that it is caused by it.
Thanks for sharing this information and guidelines for disabling Java, just one question will i be able to watch online videos?
@jacob0russell:disqus Adobe Flash Player is what you usually need in order to watch online videos on most of the video streaming websites, such as YouTube, Hulu, etc.
Now, if only I could stop my mom from freaking out everytime she sees javaSCRIPT…
Yes, I know it sounds the same. So do ‘butter’ and ‘gutter’, but I wouldn’t put the latter on a sandwich!
In the same way, when cybercriminals discovered the security flaw in Java plug-ins, they started exploiting it to infect computers and fulfill their malicious intents.
Amazing submit admin thank you. I located what i used to be in search of here. I’ll review entire of posts on this evening