Ransomware attacks are at an all-time high – and show no sign of letting up. According to the 2023 Ransomware Market Report, this type of cyberattack is expected to cost victims around $265 billion annually by 2031 – a sobering statistic that illustrates just how much of a problem this kind of malicious software is for the global economy.
It’s not just the financial impact of ransomware that can leave companies reeling. Suffering a security breach of any size can severely impact the reputation of the organisation in question, not to mention create unexpected downtime that can put a profit-damaging pause on their daily operations. And if details of the case get leaked into the public domain, it could take years, if not decades, for the affected business to gain back the trust of its customers and peers.
It’s difficult to quantify the effects of large-scale ransomware attacks. Further on in this article, we’ve ranked the top 11 biggest ransomware attacks of all time based on the financial hit these firms suffered and the devastating consequences they had to face during the clean-up phase. These examples are listed in no particular order – in many ways, they’re equally as shocking and as fascinating as each other!
First, though, let’s put ransomware into context by discussing how it can be rolled out into your devices or networks to begin with, and what you should do if you suspect your system is under attack.
What is ransomware, and how does it work?
Ransomware is a type of malicious software (aka malware) that encrypts a victim’s data or locks them out of their system, rendering their files – or in some cases their entire network – totally inaccessible.
Once it has made its way inside a system, ransomware often spreads across the network, encrypting data on multiple devices. This encryption is typically very strong, making it nearly impossible to decrypt the files without the attacker’s private key.
Once the system has been fully encrypted, the ransomware displays a message demanding payment to decrypt the files. This message often includes a deadline for payment and threatens to permanently delete the data or increase the ransom if payment isn’t made within the specified time.
If the victim pays the ransom (though this is not recommended, for reasons we’ll discuss later), they might receive a decryption key. However, there’s no guarantee that the attacker will provide the key, or that it will work as promised.
Typically, the ransom is requested in cryptocurrency, which makes the transaction harder to trace and the perpetrator more difficult to track down. And in some cases, there’s no resolution. The attacker doesn’t always follow through on their promise to restore the system once they have been compensated, leaving the business or individual out of pocket and still unable to access their personal or sensitive data.
How can ransomware be used to infect a system?
Though there are many routes that cybercriminals can take to executing a successful attack, ransomware is generally deployed through:
Phishing emails
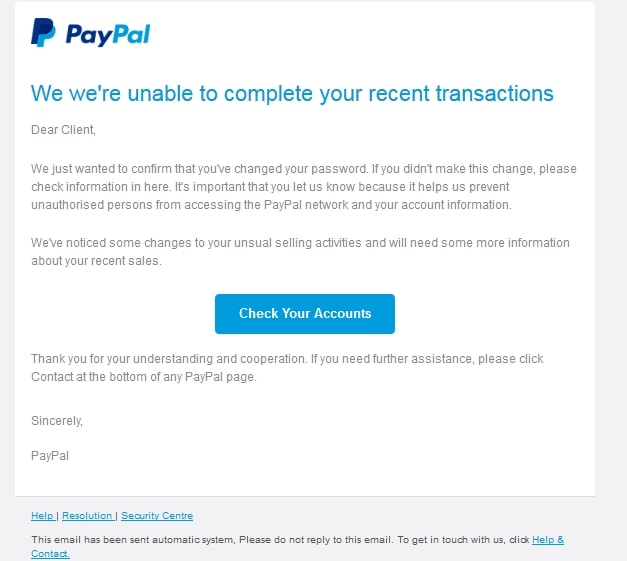
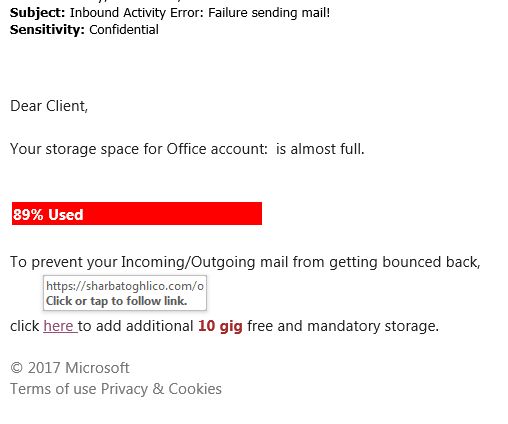
Many people are accustomed to opening emails and attachments without verifying their authenticity first, which means attackers can easily deliver ransomware by sending a message with malicious files included or a link to an app that will download the malware onto the recipient’s device.
The emails will appear to be from a legitimate source, but if you look a little closer, there will usually be some subtle errors that will give the game away. Unfortunately, many of us haven’t got time to scrutinize every last letter, leaving cybercriminals to routinely take advantage of just how busy we are.
Malicious downloads
Ransomware can be embedded in software, applications, or files that are available on the internet. When users download and install these programs or files, the ransomware is also installed on their systems.
It’s an effective means of getting people to unknowingly infect their devices, because it’s easy to accidentally download software from unofficial sources or click on advertisements that lead to malicious sites.
Vulnerabilities in outdated software
Many individuals and organizations delay or neglect updating software, leaving known vulnerabilities open for exploitation. Not having the latest patches and updates installed could cost them access to their entire network.
Remote Desktop Protocol (RDP)
Sadly, RDP has become a well-known ransomware gateway. Attackers can impersonate colleagues or IT support workers before being given the opportunity to implant the ransomware directly onto company computers.
What happens next?
Once they’ve realized they have been targeted with a ransomware attack, victims usually have the following options:
Disconnect the computer from the network
Isolating the device will stop the ransomware from scanning the network for vulnerabilities and infiltrating the wider system. Don’t reboot your computer, as this could delete any copies of the malware’s encryption keys that have been stored in the memory. If a machine only ends up being partially encrypted – because, for example, the process has been blocked by something like a permission issue – the last thing you want to do is restart it and get it to finish the job!
Pay the ransom
Though it might be tempting to fix the situation quickly with a lump sum payment, cybersecurity experts and law enforcement agencies agree that you should avoid paying the ransom request at all costs.
First of all, as we’ve already mentioned, there’s no guarantee that your attackers will provide the decryption key; they could simply take your money and move on. By paying up, you’re giving these cybercriminals the funds they need to continue and expand upon their operations, so from a moral standpoint, you’re feeding the problem. You’re also establishing yourself as a ‘good’ payer, so you’re more likely to be targeted again in the future.
Remove the malware
A great idea in principle – but something that can be difficult to execute. Some websites do offer decryption tools for certain strains of ransomware, and sometimes it’s possible to use a reputable anti-malware or antivirus software to scan and remove the offending file or code. In other cases, you will need to manually delete malicious files or entries from the registry, but this can be complex and risky.
What are the top 11 ransomware attacks of all time?
In no particular order, the team here at SUPERAntiSpyware rates the below ransomware attacks as the most devastating of all time:
- NotPetya (2017 – Financial Loss: approx. $10 billion)
- WannaCry (2017 – Financial Loss: approx. $4 billion)
- GandCrab (2018 – Financial Loss: approx. $2 billion)
- Locky (2016 – Financial Loss: approx. $1 billion)
- Costa Rican Government (2022 – Financial Loss: approx. $30 million/day)
- Ryuk (2018 – Financial Loss: approx. $150 million)
- REvil/Sodinokibi (2019 – Financial Loss: approx. $70 million)
- SamSam (2016 – Financial Loss: approx. $6 million)
- Colonial Pipeline (2021 – Financial Loss: approx. $4.4 million)
- CryptoLocker (2013 – Financial Loss: approx. $3 million)
- AIDS Trojan (1989 – Financial Loss: approx. $189-$378 per victim)
Let’s dive into each of them in more detail.
AIDS Trojan
Year: 1989
Type: Encryption ransomware (floppy disk delivery)
Attacker: Dr Joseph Popp
Target: Attendees of the World Health Organization’s AIDS conference
Losses: $189-$378 ransom per victim; limited economic impact
Current Status: Historic, not active
Otherwise known as the PC Cyborg, the AIDS Trojan was the first recorded ransomware attack.
Back in the late 80s, it wouldn’t have been possible to spread malware codes via the internet – so the perpetrators used floppy disks to target the subscriber list of a World Health Organization AIDS conference instead. By accessing the floppy disk, victims were unknowingly releasing malware onto their computers.
The ransom itself wasn’t a significant sum; the attacker only asked for between $189 and $378 to release the encrypted files. But the case proved what was possible and likely inspired many would-be cybercriminals to try their luck.
CryptoLocker
Year: 2013-2014
Type: Encryption ransomware
Attacker: Evgeniy Mikhailovich Bogachev
Target: Various Windows users
Losses: Approximately $3 million in ransom payments
Current Status: Neutralized in May 2014 (Operation Tovar)
An excellent example of ransomware that works Trojan-style via malicious email attachments, CryptoLocker code affected hundreds of thousands of Windows customers when it was first released in September 2013.
Once the infected document or ZIP file had been opened, CryptoLocker installed itself on the user’s computer – and quickly searched for any connected network drives for a wide range of file types (documents, images, etc.). It then encrypted these files using strong RSA and AES encryption algorithms.
CryptoLocker displayed a ransom note on the victim’s screen demanding payment in Bitcoin or other forms of cryptocurrency in exchange for the private decryption key, which was stored on a remote server controlled by the attackers. The ransom amount was typically between $100 and $300 (though it varied), and victims were given a limited amount of time – usually 72 hours – to pay.
In June 2014, an international law enforcement operation known as “Operation Tovar” targeted the Gameover ZeuS botnet, which was responsible for spreading CryptoLocker. The operation successfully took down the infrastructure behind both the botnet and CryptoLocker. As a result of the takedown, CryptoLocker’s servers were seized, making it impossible for the ransomware to communicate with its control servers and neutralizing the threat.
Colonial Pipeline
Year: 2021
Type: DarkSide RaaS (Ransomware as a Service)
Attacker: DarkSide
Target: Colonial Pipeline (US fuel pipeline)
Losses: $4.4 million paid, $2.3 million recovered
Current Status: DarkSide infrastructure reportedly shut down
Large ransomware attacks don’t just affect companies – they can impact the lives of everyday Americans.
The Colonial Pipeline ransomware attack was a high-profile cybersecurity incident that took place in May 2021. It targeted Colonial Pipeline, one of the largest fuel pipeline operators in the United States, which supplies nearly half of the East Coast’s fuel, including gasoline, diesel, jet fuel, and heating oil. The attack had wide-reaching consequences, impacting fuel supply and prices across several states.
How was this allowed to happen? Well, investigators eventually determined that attackers gained access to Colonial Pipeline’s IT systems through a compromised password. It was later revealed that this password was linked to an inactive VPN account that did not use multi-factor authentication (MFA), making it easier for the attackers to infiltrate the system.
Once inside the network, the DarkSide group deployed ransomware that encrypted Colonial Pipeline’s data, rendering it inaccessible to the company. The ransomware affected the company’s business networks, not the operational technology (OT) systems directly responsible for pipeline operations – but the firm decided to shut down its entire pipeline system, putting a stop to fuel distribution along the East Coast and causing chaos at gas stations in the region.
Against standard advice, Colonial Pipeline decided to pay the ransom of $4.4 million to the malware’s creators, DarkSide, to regain access to their systems and restore operations.
SamSam
Year: 2016-2018
Type: Manual deployment
Attacker: BOSS SPIDER Group
Target: Over 200 victims, including municipalities and hospitals
Losses: Over $6 million in ransom payments
Current Status: Historic, not active
Unlike typical ransomware that spreads through phishing emails or malicious downloads, SamSam attacks were carefully planned. The attackers typically gained initial access to their targeted networks by exploiting vulnerabilities in remote desktop protocol (RDP) services or Java-based web servers, or by stealing credentials. Once inside the network, the attackers manually moved laterally across the systems, identifying key servers and systems to target.
The ransomware encrypted important files and databases. The attackers often timed the deployment during off-hours to avoid immediate detection and ensure widespread encryption before the organization could respond.
The ransom amount varied, but it was typically in the range of tens of thousands of dollars, with some demands reaching hundreds of thousands (payable in Bitcoin). Cheekily, the attackers often offered a discount for quick payment or additional fees if the payment was delayed.
SamSam was responsible for the notorious 2018 ransomware attack on the City of Atlanta, which crippled several city services, including the court system, law enforcement, and public records. The attackers demanded a ransom of approximately $51,000 in Bitcoin. The city refused to pay, resulting in significant recovery costs that have been estimated to exceed $2.6 million.
REvil/Sodinokibi
Year: 2019 – 2021
Type: RaaS (Ransomware as a Service)
Attacker: REvil Group
Target: Various, including Kaseya, JBS
Losses: Demanded $70 million for universal decryption
Current Status: Group’s infrastructure disrupted in 2021
This ransomware caused big problems for organizations in the finance, healthcare, legal, IT, and critical infrastructure sectors, among others.
Interestingly, REvil operated as a RaaS, meaning that the creators of the ransomware provided the software to “affiliates” who would carry out the attacks. The affiliates would receive a share of the ransom payments, typically around 60-70%, while the remaining percentage would go to the REvil developers. This model enabled REvil to scale rapidly.
And, as well as deploying encryption, REvil became known for exfiltrating data before encryption. This gave them additional leverage, as they could threaten to publicly leak the stolen data if the ransom was not paid. In fact, REvil helped to set the trend for combining data encryption with data theft.
REvil caused widespread destruction across many industries and was responsible for shutdowns and significant loss of revenue for companies such as Travelex, JBS Foods, Kaseya VSA, and the New York based law firm Grubman Shire Meiselas & Sacks. Bitcoin/Monero payment demands were huge, reaching as high as $70 million.
Ryuk
Year: 2018-present
Type: Encryption ransomware
Attacker: WIZARD SPIDER Group
Target: Various, mostly large organizations
Losses: Estimated over $150 million
Current Status: Still active
Like REvil and SamSam, Ryuk affected – and continues to affect – larger organizations and government departments.
Ruk attacks often start with a phishing email or an infection through other malware, such as TrickBot or Emotet, which establish a foothold in the network. Once inside the system, attackers move across the network to gain access to more data, often compromising administrative accounts to maximize the damage. Ryuk then encrypts files on the compromised systems with their famous “.ryk” extension .
Ryuk targets a wide range of file types, including databases, backups, and documents critical to business operations. Then, as is standard practice, a ransom note is left on the affected systems, demanding payment in Bitcoin.
Several US cities, including Baltimore and New Orleans, have been targeted by Ryuk, causing significant disruptions to city services. This ransomware – which is thought to be operated by a group called Wizard Spider – has been particularly damaging to healthcare institutions, where the encryption of patient records and other vital systems can have life-threatening consequences.
Costa Rican Government
Year: 2022
Type: Encryption ransomware
Attacker: Conti gang
Target: Costa Rican government institutions
Losses: Estimated $30 million/day
Current Status: Group’s infrastructure disrupted
Several years ago, the Russia-based Conti ransomware group launched a coordinated attack on the Costa Rican government, bringing its operations across its Ministry of Finance and its Ministry of Labor and Social Security to a halt.
Critical tax collection, customs processing and payment services were inaccessible, so officials were desperate to resolve the situation. Conti initially demanded a $10 million ransom, which was later increased to $20 million as the group intensified its threats. They also began leaking sensitive data from the compromised systems when the ransom was not paid.
In response to the scale and impact of the attack, Costa Rican President Carlos Alvarado declared a national emergency on May 8, 2022. Other countries took note, aware for perhaps the first time of the scale of destruction ransomware can leave in its wake.
Locky
Year: 2016-2018
Type: Encryption ransomware (phishing emails)
Attacker: Possibly Dridex hackers (Evil Corp or TA505)
Target: Various, predominantly healthcare providers
Losses: Estimated $1 billion
Current Status: Historic, not active
Locky ransomware first came onto the scene in February 2016. It was initially distributed through large-scale phishing email campaigns, with these emails containing malicious attachments that were disguised as invoices or other seemingly ‘official’ documents. When opened, the attachment would execute a macro that downloaded and installed the Locky ransomware on the victim’s system, and from there, the malware would begin encrypting all kinds of file types with its trademark ‘.locky’ extension.
Locky quickly became one of the most widespread ransomware threats, affecting individuals, businesses, and organizations around the world. It caused significant disruptions to businesses but also notably the healthcare sector.
Over time, several variants of Locky were released, each with different encryption methods or file extensions, making detecting and defending against the ransomware more challenging. However, it has since faded from use, having been replaced by more sophisticated strains.
GandCrab
Year: 2018-2019
Type: RaaS (Ransomware as a Service)
Attacker: PINCHY SPIDER Group
Target: Various, including businesses and individuals
Losses: Estimated $2 billion extorted
Current Status: Group claimed to have retired in 2019
Emerging in 2018, GandCrab ransomware was one of the most prolific types of ransomware before it eventually entered retirement just over a year later in 2019.
Like REvil, GandCrab was offered as a Ransomware-as-a-Service (RaaS) on darknet forums, meaning that the developers of GandCrab allowed other cybercriminals to distribute the ransomware in exchange for a share of the ransom payments.
As well as being distributed via – you guessed it! – phishing emails, GandCrab was distributed via exploit kits such as RIG and GrandSoft, which would infect vulnerable systems when users visited compromised or malicious websites. GandCrab operators also exploited weak or exposed RDP connections to gain access to networks and deploy the ransomware. From smaller outfits to larger enterprises, GandCrab didn’t discriminate when it came to the kinds of businesses it targeted.
Experts estimate that GandCrab operators earned over $2 billion in ransom payments over its operational period, making it one of the most profitable ransomware families in history.
WannaCry
Year: 2017
Type: Encryption ransomware (cryptoworm)
Attacker: Believed to be the Lazarus Group (linked to North Korea)
Target: Global (various organizations including the UK’s NHS)
Losses: Estimated $4 billion
Current Status: Attack mitigated with patches, but remnants may still exist
Previous ransomware is good at infecting devices one by one. WannaCry, on the other hand, is what’s known as a cryptoworm: it spreads primarily through networks.
WannaCry was a global campaign that targeted computers running the Microsoft Windows operating system, specifically those that hadn’t yet been updated with Microsoft’s latest security patches and were still vulnerable to a flaw in the Server Message Block (SMB) protocol known as EternalBlue. It’s thought to originate from a state-sponsored hacking group in North Korea.
WannaCry’s ransom note, which was handily displayed in multiple languages, gave victims a deadline of a few days to pay, after which the ransom would double. If the ransom was not paid within a week, the files would be permanently lost.
After infecting more than 230,000 computers in 150 countries and impacting huge organizations such as FedEx, Telefonica, Renault and the UK’s National Health Service, WannaCry’s rapid takeover was eventually slowed by a cybersecurity researcher who discovered a kill switch within the code. This wasn’t before WannaCry had caused billions of dollars’ worth of losses for its victims, along with, of course, mass loss of productivity and service.
NotPetya
Year: 2017
Type: Wiper disguised as ransomware
Attacker: Believed to be Russian-sponsored threat attackers
Target: Global, significant impact on Maersk and Merck
Losses: Estimated $10 billion
Current Status: Historic, not active
NotPetya has made the list because was one of the most far-reaching attacks of its nature in recent history. But what makes it different from the rest is that it was essentially a wiper, ie a type of malware that’s not only designed to encrypt data, but delete it.
NotPetya also exploited the EternalBlue vulnerability and worked to encrypt the master boot record (MBR) to cause critical damage to its affected systems and render data completely unrecoverable. It also used tools like Mimikatz to harvest credentials.
Although Ukraine was the primary target, because WannaCry originally spread due to a compromised update to the Ukrainian accounting platform MeDoc, the attack quickly spread to other countries and affected multinational corporations. Major companies hit included Maersk, Merck, FedEx’s TNT Express, and WPP, among others. There’s evidence to suggest that WannaCry was a politically motivated campaign run by hackers that were linked to Russia’s military intelligence agency.
WannaCry proved just how vulnerable critical infrastructure and global supply chains can be to complex and widespread cyber threats. It led many organizations to reassess and strengthen their cybersecurity measures.
As you can see from these ransomware examples, ransomware can strike at any time, and impact any business. New strains and types are emerging all the time, which is why it’s so crucial to make sure your computers and networks are protected against past and current threats.
SUPERAntiSpyware works around the clock to block ransomware attacks and keep your PCs free from malicious software. See how our Professional X Edition can mitigate risk in this area and form the foundations of your cybersecurity strategy.








 What Are Cookies and How do they work?
What Are Cookies and How do they work?